Got on Did It Again and Then Couldnt Find the Saved File With the Certificate
How tin can I observe the individual cardinal for my SSL document
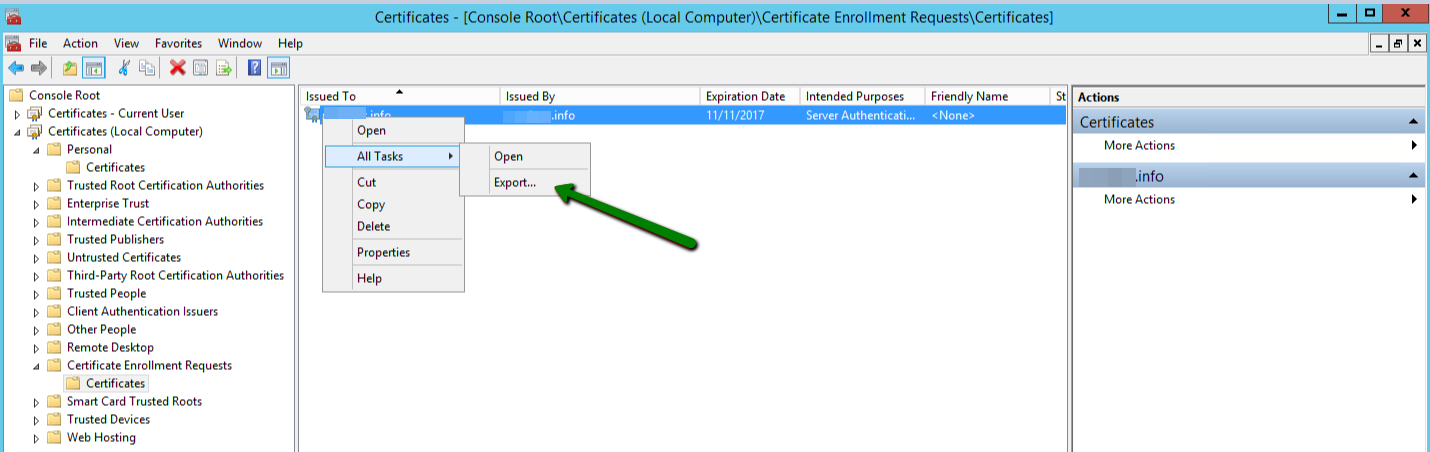
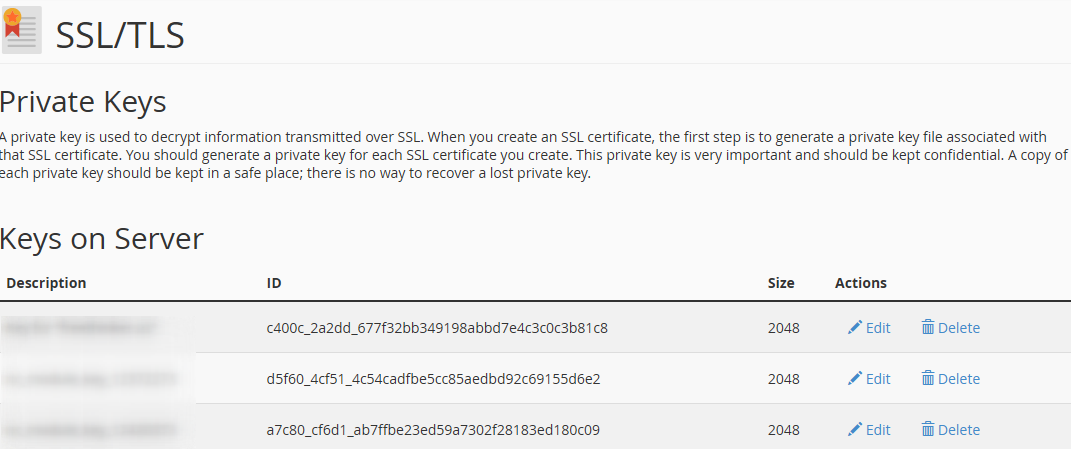
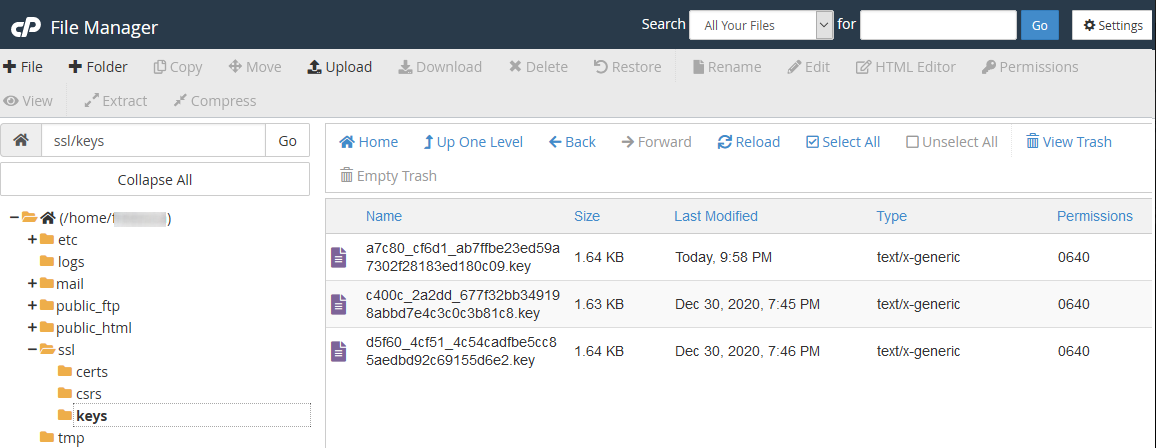
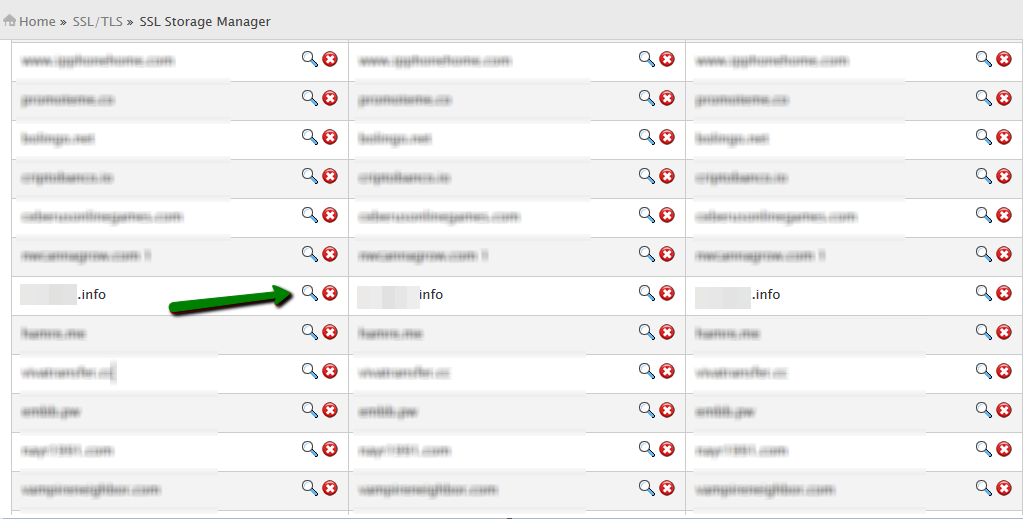
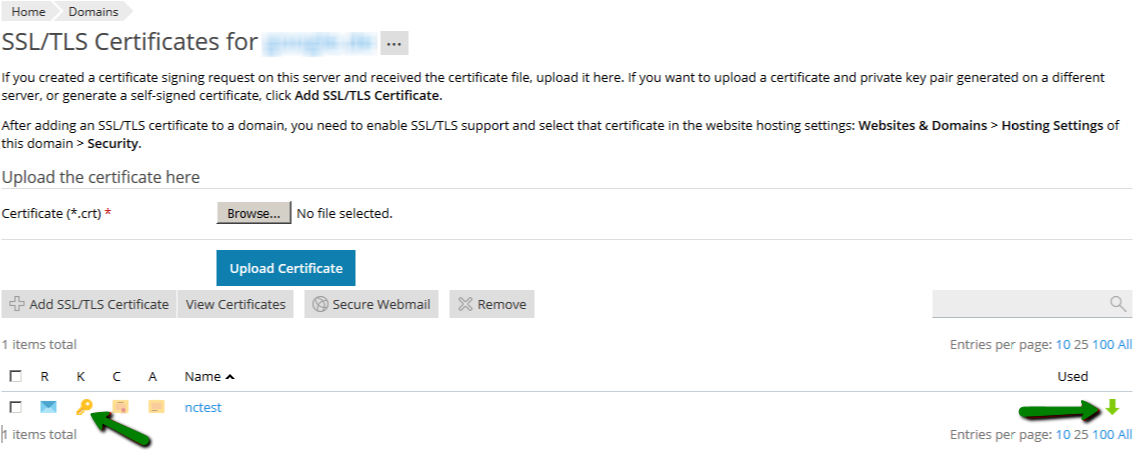
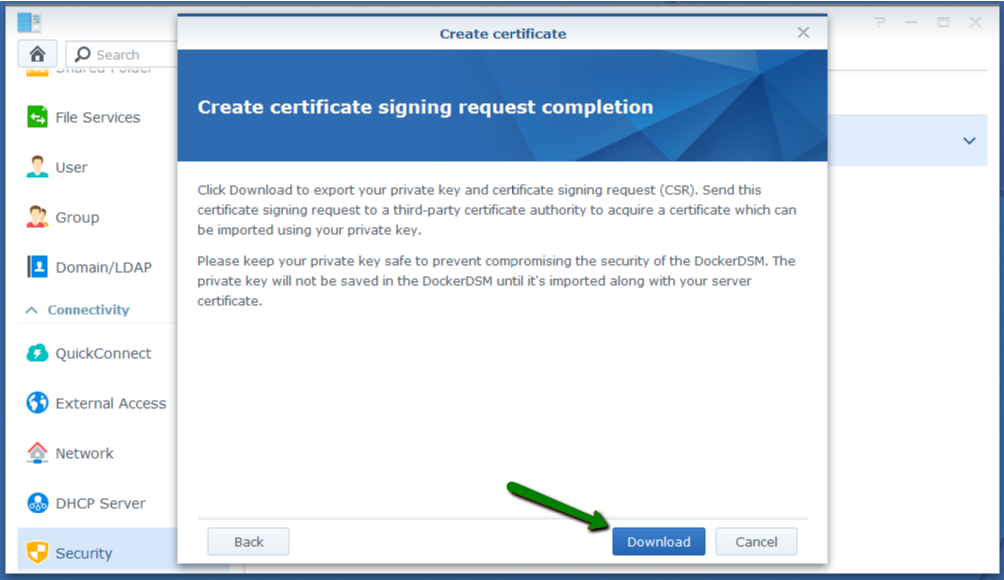
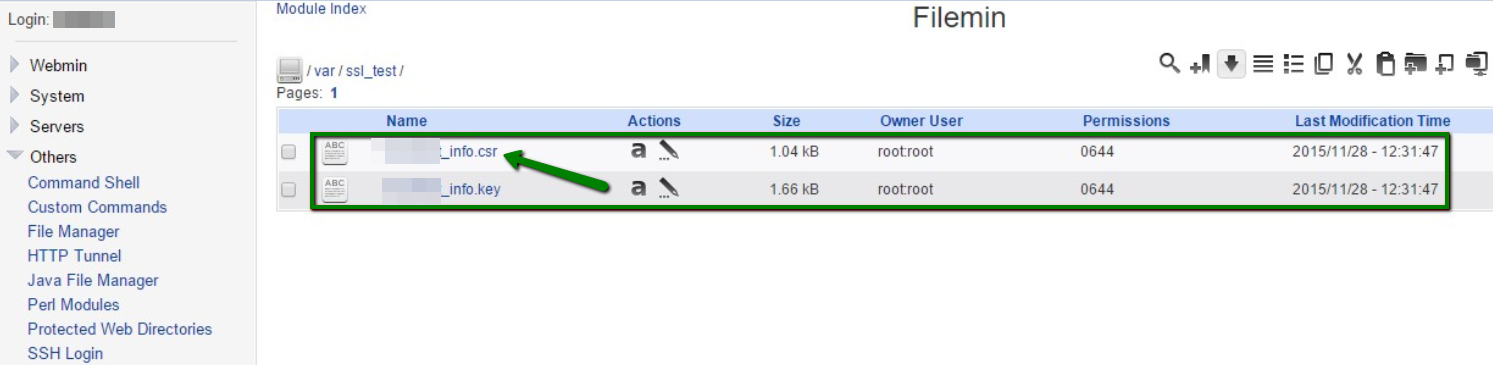
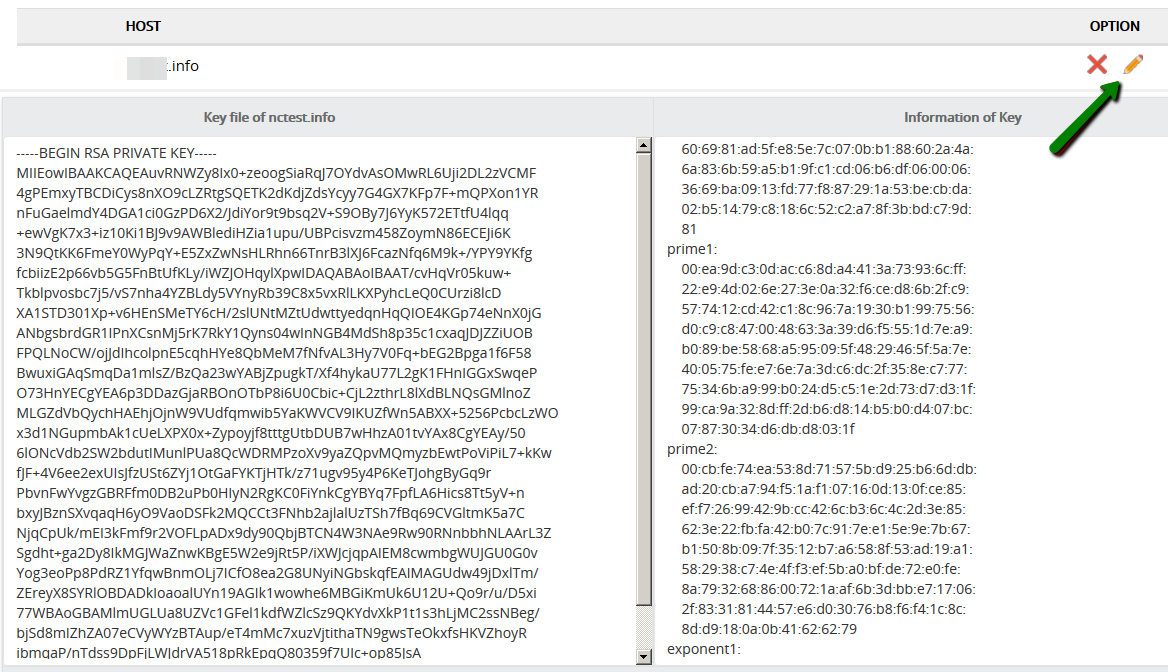
If you just got an issued SSL certificate and are having a hard time finding the respective private key, this commodity can help yous to find that one and only key for your certificate. Firstly, let's dive into nuts a little. The design of global public key infrastructure, relying on which modern secure negotiation through SSL/TLS is possible, implies that there is always a pair of unique keys - All the same, in near cases, this lawmaking won't come into your sight while generating the CSR. It is usually created in the background and silently saved in the server'southward filesystem. And obviously, during the SSL certificate installation the key should exist fetched to the certificate automatically. Nonetheless, some systems do not have such a kind of behaviour or sometimes we need to install the certificate on another server. These are the examples of the cases when nosotros really need to know the exact location of the private primal. Beneath yous can detect tips, examples and pieces of advice that you can consider to follow in lodge to get a missing puzzle and avoid certificate reissue (i.e., repeating the process of activation and validation from scratch). Linux operating systems (Apache, Nginx, Lighttpd, Heroku) Traditionally, private keys on Linux-based operating systems (Ubuntu, Debian, CentOS, RedHat, etc.) are openssl generated keys with the crypto toolkit and saved into files with the .central or .pem extension. However, since specific extensions are non obligatory for simple text files on Linux systems, the individual key lawmaking can be put into a file with almost any name. If you remember the full or partial name of the cardinal file, yous can attempt to become its location past running the 'find' command as below: sudo find [search_start_folder] -type f -iname 'private.fundamental' - [search_start_folder] parameter indicates the directory to start the search from and through all directories inside it, for example, to search from "root", the / sign should be specified; HINT: Very often, the name of the key file resembles the domain name the document is issued for, east.k., "example.com.key", "example_com.central", "example-com.key" etc. Another way to go the individual key file location is to search inside the files by sure patterns: grep -r --exclude-dir=log --exclude-dir=ssh --exclude=*history -I -l -e '-----BEGIN Individual*' -east '-----Begin RSA*' -due east '-----BEGIN EC*' [search_start_folder] 2> /dev/naught This one-liner command prints out an absolute path to the file, which contains a matching expression (------BEGIN header), for example, "/etc/ssl/private.primal". Windows operating systems (IIS, Substitution, Minor Business organization server) Windows systems do not let retrieving the private cardinal in plain text. When an SSL certificate is imported either through MMC or IIS, the matching private central is bound to the document automatically, of course, if the certificate is being imported to the same case the key was generated on. But if we need to get the private key for example for the certificate installation on another server, there is an option to export the central in a password protected file (PFX or PKCS12 format). To do so, you lot will need to open MMC Certificates snap-in in the following way: Win+R > mmc.exe > OK > File > Add/Remove Snap-in > Certificates > Add > Computer account > Next > Local computer > Finish > OK Then navigate to Document Enrollment Requests > Certificates (if the document asking was not completed) or Personal > Certificates (if the certificate request was already completed) folder, right-click on the certificate entry and click All Tasks > Export to open up the export sorcerer. More details on the export process tin be establish hither. Every bit a event, y'all will receive a .pfx file containing the central. To become the key in manifestly text, you can catechumen the .pfx into PEM encoded files using tool (PKCS#12 to PEM option). Mac Bone X The default "Keychain" tool in the Server app does not allow accessing the generated private central through the graphic user interface. However, using the command line tools in Terminal, it is possible to navigate to the "/etc/certificates" folder and open the fundamental file, which should be called something like ".key.pem". Tomcat (using keytool) Unless the SSL connector on Tomcat is configured in APR style, the private key is usually stored in a countersign-protected Coffee keystore file (.jks or .keystore), which was created prior to the CSR. To extract the key in PEM format, the keystore should be converted into .pfx/.p12 (PKCS#12) file firstly. With the "keytool" utility, it can be done with the assistance of the following command: keytool -importkeystore -srckeystore keystore.jks -destkeystore keystore.p12 -deststoretype PKCS12 -srcalias "keystore.jks" should be replaced with the name of the keystore, containing the required key; "keystore.p12" - with the proper noun of the .pfx/.p12 file the keystore will be converted into; When the .pfx/.p12 file is created, information technology can be converted into PEM formatted files either with the help of this tool (PKCS#12 to PEM option) or using OpenSSL. The OpenSSL command would be: openssl pkcs12 -in keystore.p12 -nocerts -nodes -out individual.key - 'private.key' refers to the name of the file the individual central text will be saved to. cPanel In that location are 2 ways to get to the Private central in cPanel: On the cPanel domicile page, click on "SSL/TLS Manager" and then on the "Private keys" push button. On the new screen, y'all should run into the list of the Individual keys whenever created in a particular cPanel account. Clicking on the the "View & Edit" button will open the screen presenting the key in both encoded and decoded forms: Click on the File director push from the cPanel home screen and open up the window like on the screenshot below. Side by side, you volition need to find the "ssl" folder and then click on the "key" directory inside it. The private keys will announced in the right-side navigation console. Then the required fundamental file can exist either downloaded or opened in plain text: WHM In WHM the private keys are stored along with the corresponding CSRs and certificates in "SSL Storage manager". To go at that place, you can click "SSL/TLS" on the home screen and so on the "SSL Storage manager". To open up the private central text, you will need to click on the magnifier button in the starting time column called "Central". Plesk Afterwards navigating to Domains > domain.com > SSL/TLS certificates, you should meet the page similar to the i on the screenshot below. The key sign with the message "Private central office supplied" indicates the presence of the needed key in the arrangement. To open information technology in plainly text, you will demand to click on the proper name of the entry and curl down until the key code appears on the screen. Alternatively, you tin can click on the green arrow sign on the right and download the .pem file containing the primal, the CSR and the certificate along with the CA bundle, if they were imported already. The .pem file can be opened with any text editor similar Notepad: Synology NAS DSM In Synology DSM, the private primal is downloaded in the annal.zip file on the concluding stride of the CSR generation sorcerer. It is saved in the server.key file within the .nada archive and can be opened on a local computer with a text editor: Webmin The Webmin panel was designed equally a graphic user interface on top of the control line tools, although it comes with the File managing director (Filemin) which can exist used for browsing the file system in order to find the key file, which was created by the OpenSSL command in Command Shell when the CSR was generated. The other way to detect the private key in Webmin is to open "Command shell" under the "Others" department and run the "find" or "grep" control from the "Linux operating systems" paragraph of this article. VestaCP The private key on VestaCP is not saved anywhere throughout the user interface; it is necessary to save the fundamental text into a local file during the CSR generation. However, in that location is all the same a take chances to detect it through SSH. When VestaCP creates a new CSR, the Private key is stored equally a temporary file in the "/tmp" directory. The absolute path to the key file might look similar "/tmp/tmp.npAnkmWFcu/example.com.fundamental", for case. The main bottleneck hither is that the files inside "/tmp" are deleted permanently during each server reboot. To go the location of the key file on your example, the following command tin exist invoked: find /tmp -type f -iname 'domain.com.key' - "domain.com" should exist replaced with the bodily domain name the CSR was generated for. Alternatively, the same former "grep" can be used as well: DirectAdmin In the recent versions of DirectAdmin console the private key is usually saved in the system and gets pre-fetched in the "Paste a pre-generated document and key" department in the SSL Certificates menu. If during the document installation you are about to paste the document text under the auto-populated private key text only see an empty window, it could mean the CSR code was generated elsewhere or the private key was not added to this window due to a arrangement glitch. In the latter example, it is possible to think the key via SSH. It is normally saved in the following directory: /usr/local/directadmin/data/users/ Webuzo The "SSL" section in Webuzo is located on the habitation page. Clicking on the "Individual keys" push volition lead to the list of the generated keys. To meet the fundamental text, the pencil button should exist clicked on the right side of the list under the "Option" column: In decision, if none of the higher up-mentioned tips were helpful and the original private key cannot be retrieved, it is necessary to generate the new CSR / private key pair and reissue the certificate, making sure that the individual key is safety this time.What is a Individual Key?
Public central vs private cardinal
Public primal is embedded in the SSL certificate and individual cardinal is stored on the server and kept secret. When a site visitor fills out a class with personal information and submits information technology to the server, the data gets encrypted with the public key to protect if from eavesdropping. On the server this data is decrypted by the private key and passed over for further processing. To ensure that nobody else tin can decrypt the transmitted message, we must utilise a unique and unforgeable pair of keys. So in a nutshell, ane key without another is useless. How exercise you generate a private key?
The private key is generated simultaneously with the CSR (certificate signing request), containing the domain name, public cardinal and additional contact data. The CSR is to be sent to the document say-so for validation and signing immediately after the document activation in the Namecheap user account panel. The individual key must be kept hole-and-corner, ideally on the same server the document will exist installed on. Tin can I generate a new private key for my SSL certificate?
Since a public key with the boosted information (i.e., domain proper name and administrative contact information) must be signed past a trusted document authority in society to make it applicable and legitimate for securing communication with your server, it wouldn't make much sense if we could only make up a new private key for an already validated public key. On the other mitt, we must be sure that nobody tin create a matching private key basing on a public key. Thus, mod cryptosystems make such a job most impossible. What does a individual primal look similar?
Individual key is an encoded piece of data, usually a few dozen lines of randomly looking symbols, enclosed with the headers similar to these ones: -----Begin RSA PRIVATE KEY----- and -----END RSA PRIVATE Cardinal-----
How to retrieve a misplaced private key
It depends on a certain server operating system and whether CLI (control line interface) or a spider web-hosting control panel of a particular blazon was used for CSR generation. And here comes the main part. How to recall a private key on dissimilar server platforms:
- to practice the search by a partial filename, the assumed proper name of the file should exist specified with an asterisk (*), for example, the "*.key" value allows locating every file with the proper name ending with ".key".
grep -r -I -l -eastward '-----Begin Private*' -e '-----Brainstorm RSA*' /tmp 2> /dev/zero
Source: https://www.namecheap.com/support/knowledgebase/article.aspx/9834/69/how-can-i-find-the-private-key-for-my-ssl-certificate/
0 Response to "Got on Did It Again and Then Couldnt Find the Saved File With the Certificate"
Post a Comment